In addition to log data they can take in data from idss vulnerability assessment products and many other security tools to centralize and speed up the.
Security log management procedure.
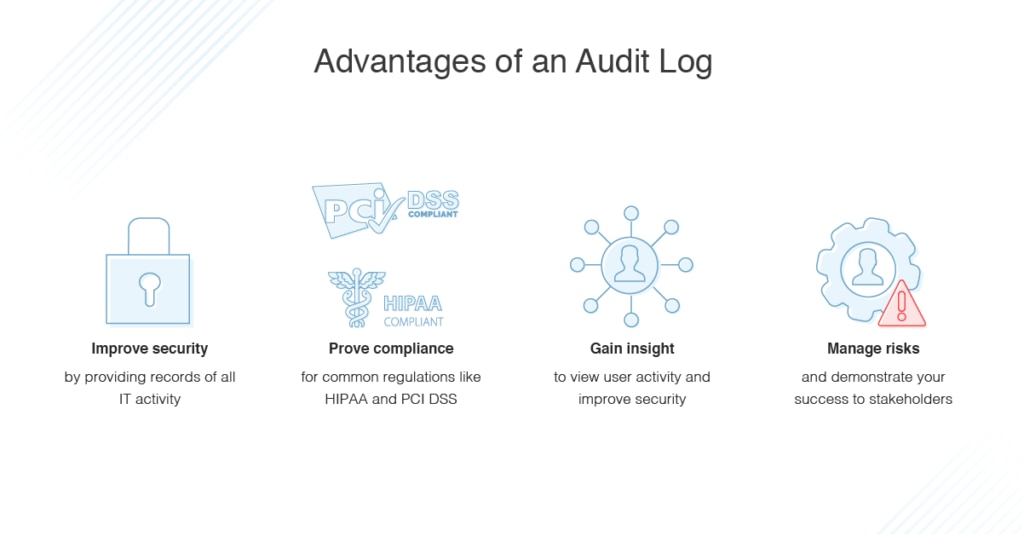
For security logs to be useful in the defense of information.
Routine log analysis is.
But having security logs without procedures to actively review and analyze them is of little use in the ongoing management of information security defenses and is the modern equivalent of fortress walls without watchmen.
Each event in a network generates data and that information then makes its way into the logs records which are produced by operating systems applications and other devices.
Log management has evolved from standalone syslog servers to complex architectures for security event information management.
Here s a high level overview of how logs work.
Acronyms used for these blend together as sem sim and seim.
Need for computer security log management the process for generating transmitting storing analyzing and disposing of computer security log data.
Ucsc information technology services log procedures introduction.
The national institute of standards and technology nist developed this document in furtherance of its statutory responsibilities under the federal information security management act fisma of 2002 public law 107 347.
This publication seeks to assist organizations in understanding the need for sound computer security log management.
It provides practical real world guidance on developing.