As attackers are becoming faster.
Security automation and orchestration open source.
In the never ending quest to stay ahead of cyberattackers a growing number of enterprises are turning to a relatively new category of security tools.
Security automation helps it teams increase mean time to response and handle intrusion threats faster and more efficiently.
Cortex xsoar is the industry s only extended security orchestration automation and response platform that unifies case management automation real time collaboration and threat intelligence management to transform every stage of the incident lifecycle.
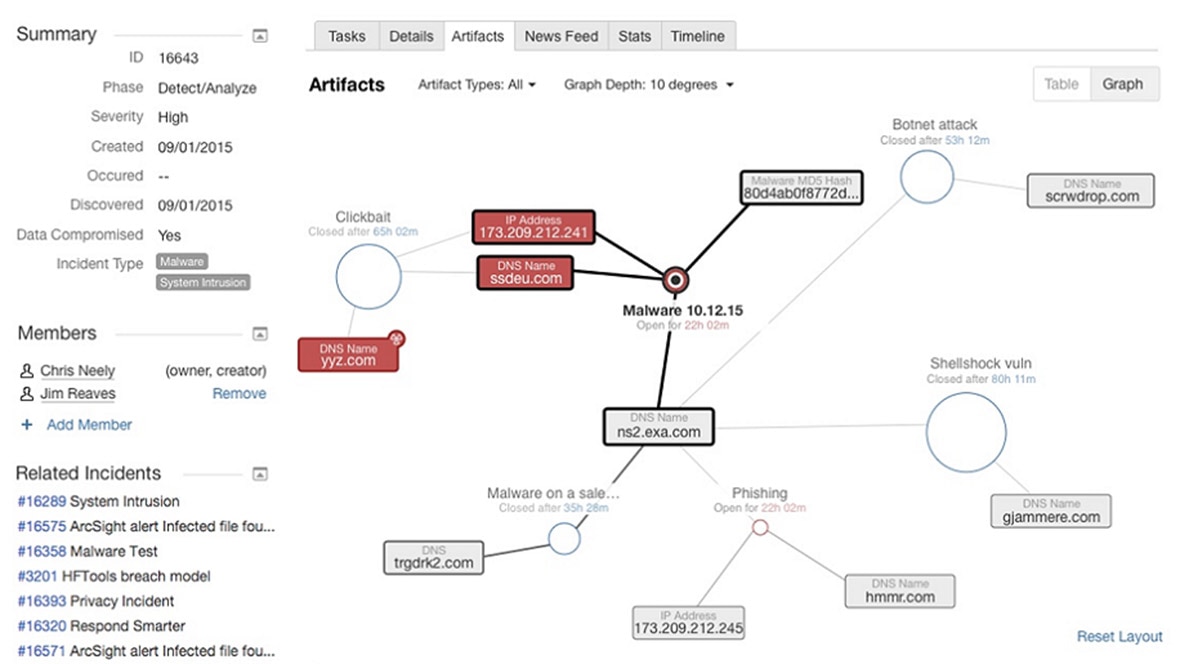
Soc analysts are becoming worn down due to the growing amount of cyber security threats ongoing alert fatigue and the industry skill shortage that is leaving socs understaffed.
There are many different orchestration tools that can help you with cloud orchestration.
Patrowl open source free and scalable security operations orchestration platform patrowl patrowldocs.
Rsa conference 440 views.
By automating your incident response soc teams can improve performance and save time.
Automation of a variety of tasks both routine and complex frees up much needed analyst time and accelerates the whole incident response process.
It eliminates many of the manual processes involved in deploying and scaling.
Patrowl open source free and scalable security operations orchestration platform smart security camera 104 a pi zero and motion based webcamera that forwards images to amazon web services for image processing.
If you re after container orchestration kubernetes is an open source platform that automates linux container operations.
Doing security orchestration automation and response before it was born duration.
Open source security best practices for developers.
With the proliferation of single point security solutions in the marketplace today it s no surprise that it teams struggle to efficiently monitor the security of their environments.
Red hat ansible automation platform is one option.
Security automation and orchestration solutions.