The tsp secure project is a joint effort of the sei s tsp initiative and the sei s cert program.
Secure software development best practices would you suggest to improve software security.
So learn the 3 best practices for secure software development.
Five software development practices that you can apply immediately to improve application security.
But with cyber attack and malicious threats common in software industry it is very essential for an enterprise to think about the security of their most sensitive data.
Sast and dast solutions aren t substitutes for secure coding practices but they will help.
That s why it s important to ensure a secure software development process.
Using veracode to test the security of applications helps customers implement a secure development program in a simple and cost effective way.
The best practices in the coding phase of a secure sdlc revolve around educating the developers.
These stakeholders include analysts architects coders testers auditors operational personnel and management.
Instead of focusing only on language or platform specific problems developers need an insight.
In the wake of high profile data breaches and the exploitation of operational security flaws.
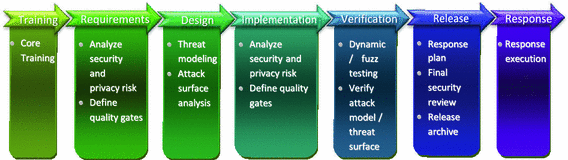
The principal goal of the project is to develop a tsp based method that can predictably produce secure software.
Given below is a compilation of ten best practices for secure software development that reflect the experience and expertise of several stakeholders of the software development life cycle sdlc.
Secure software development is essential as software security risks are everywhere.
Protect the brand your customers.
Acknowledging these concerns a review of the secure software development processes used by safecode members reveals that there are corresponding security practices for each activity in the software development lifecycle that can help to improve software security.
Tsp for secure software development tsp secure extends the tsp to focus more directly on the security of software applications.
This will minimize your cybersecurity risk exposure.
A 100 secure software development is almost impossible as no software can be made fully protected.
These practices are agnostic.
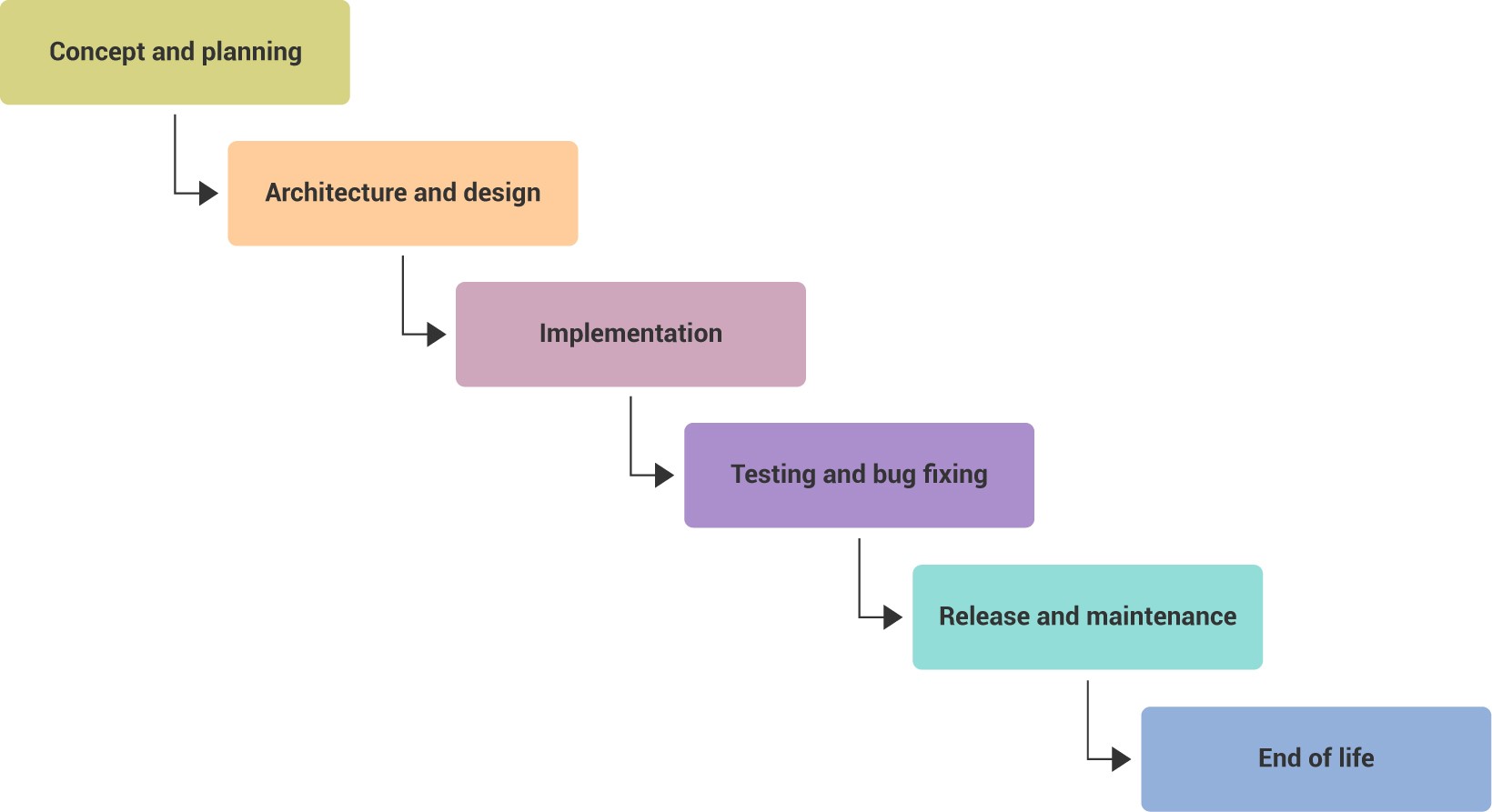
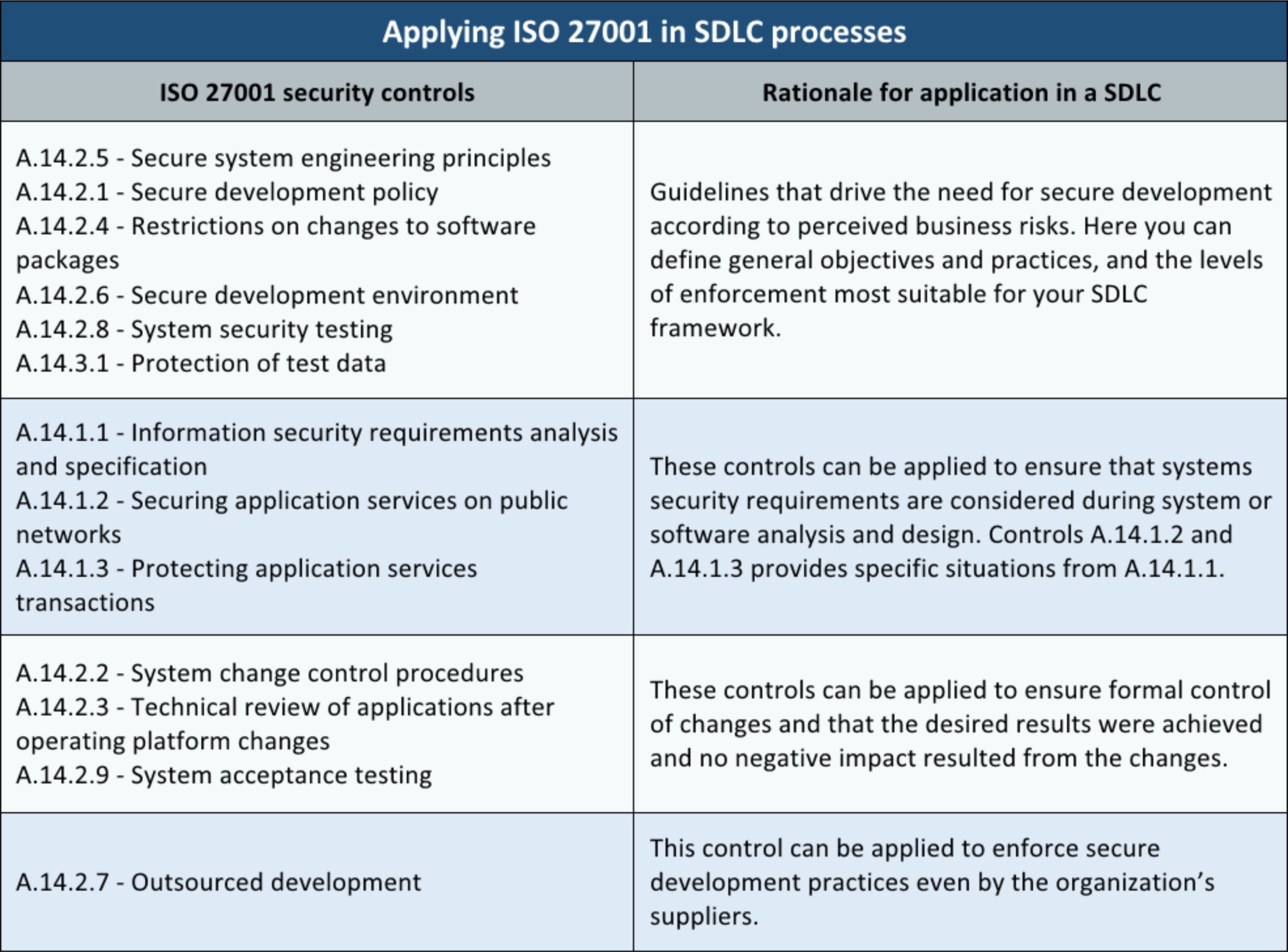
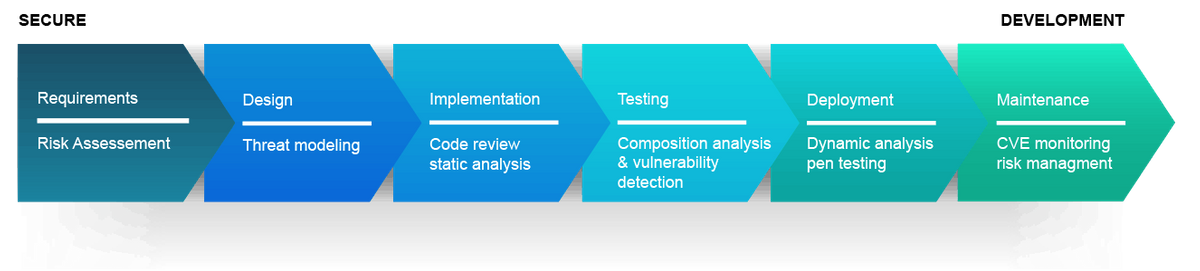
Secure development lifecycle sdlc integrating security practices into the software development lifecycle and verifying the security of internally developed applications before they are deployed can help mitigate risk from internal and external sources.
However by following certain best practices a secure.