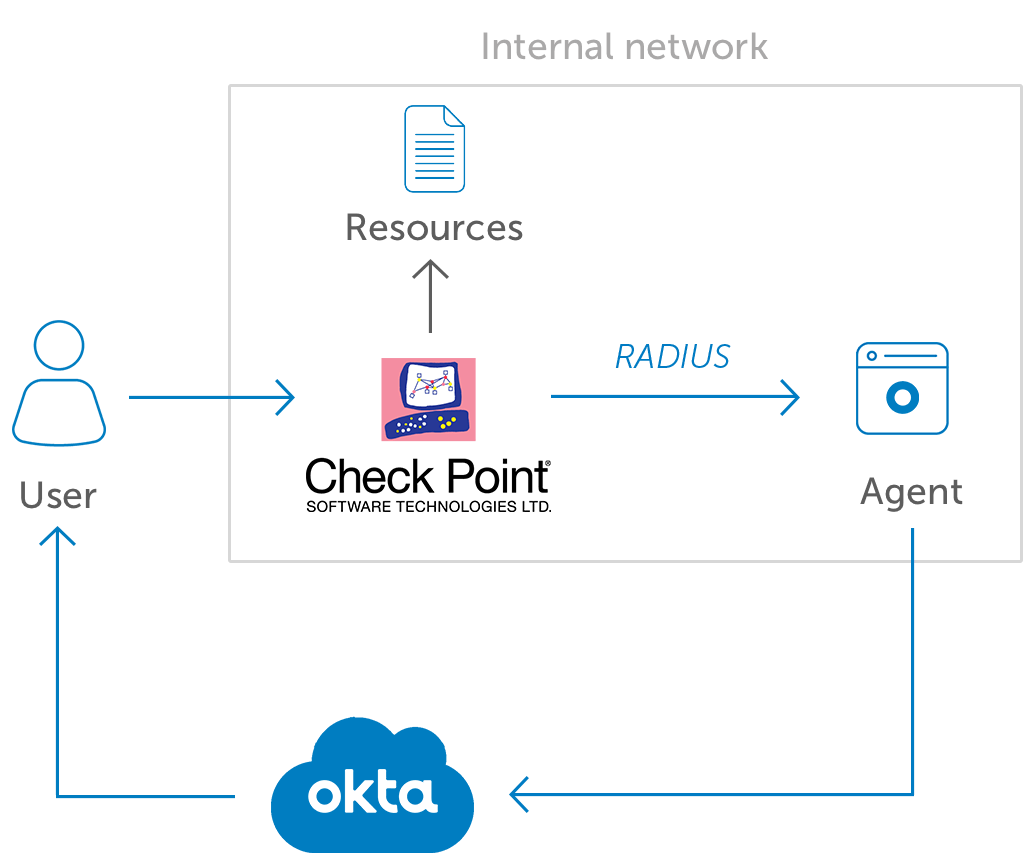
All remote users who access chi applications including outlook and skype for business from a laptop must connect to our network via vpn and be registered for our secure remote access two factor authentication tool.
Secure remote access chi.
However sometimes the right way to act is unclear.
Use by unauthorized persons is prohibited.
Can be initiated.
If you are accessing an application for which secure remote access is enabled and you have not registered to use secure remote access you will see an access denied message.
If you need assistance meeting these requirements please contact the its service desk live chat or 866 236 0441.
Remote access portal home.
If this is your first time logging in please register using the register here link below.
Luke s health information management policies and procedures must be strictly followed.
Contact chi health at home its service desk at 866 445 8648.
For registering for chi easy access for using it for password changes resets and account unlocks.
Chi applications require secure remote access duo.
Following chi easy access registration or.
Support for ethical decision making is always available to chi employees.
Luke s health company business.
Single sign on sso simplify and streamline secure access to any application.
Duo access secure access with sso and detailed device visibility.
Of calling the its service desk for signing up for duo secure remote access s o you can confirm your identity should you need to call the its service desk for helping save yourself time and hassle and reducing chi s costs.
Duo mfa secure access with an overview of device security.
Secure remote access is already in use in many instances across chi and its is continuing implementation of this tool.
Secure remote access is already in use in many instances across chi and its is continuing implementation of this tool.
Duo beyond zero trust security for all users devices and apps.
Secure remote access registration.
This is a private system operated for chi st.
Remote access secure access to all applications and servers.
From the secure remote access enrollment portal accessible on insidechi.
Will also be initiated when you access a secure remote access enabled application or website.
Secure remote access how to enroll a device verified.
If you are accessing an application for which secure remote access is enabled and you have not registered to use secure remote access you will see an access denied message.
Use the form on the left to log in to your chi health at home or chi st.