This publication by the national institute of standards and technology provides an overview of the security and privacy challenges pertinent to public cloud computing and points out considerations organizations should take when outsourcing data applications and infrastructure to a public cloud environment.
Public cloud security standards.
The largest and arguably most comprehensive player in cloud security standards is the csa or cloud security alliance.
This set of standards is referred to as the cloud controls matrix ccm and consists of about 100 controls and.
The common characteristics most interpretations share are on demand scalability of highly available and reliable pooled computing resources secure access to metered services from nearly anywhere and displacement of data and services from inside to outside the organization.
With corporate members including amazon web services.
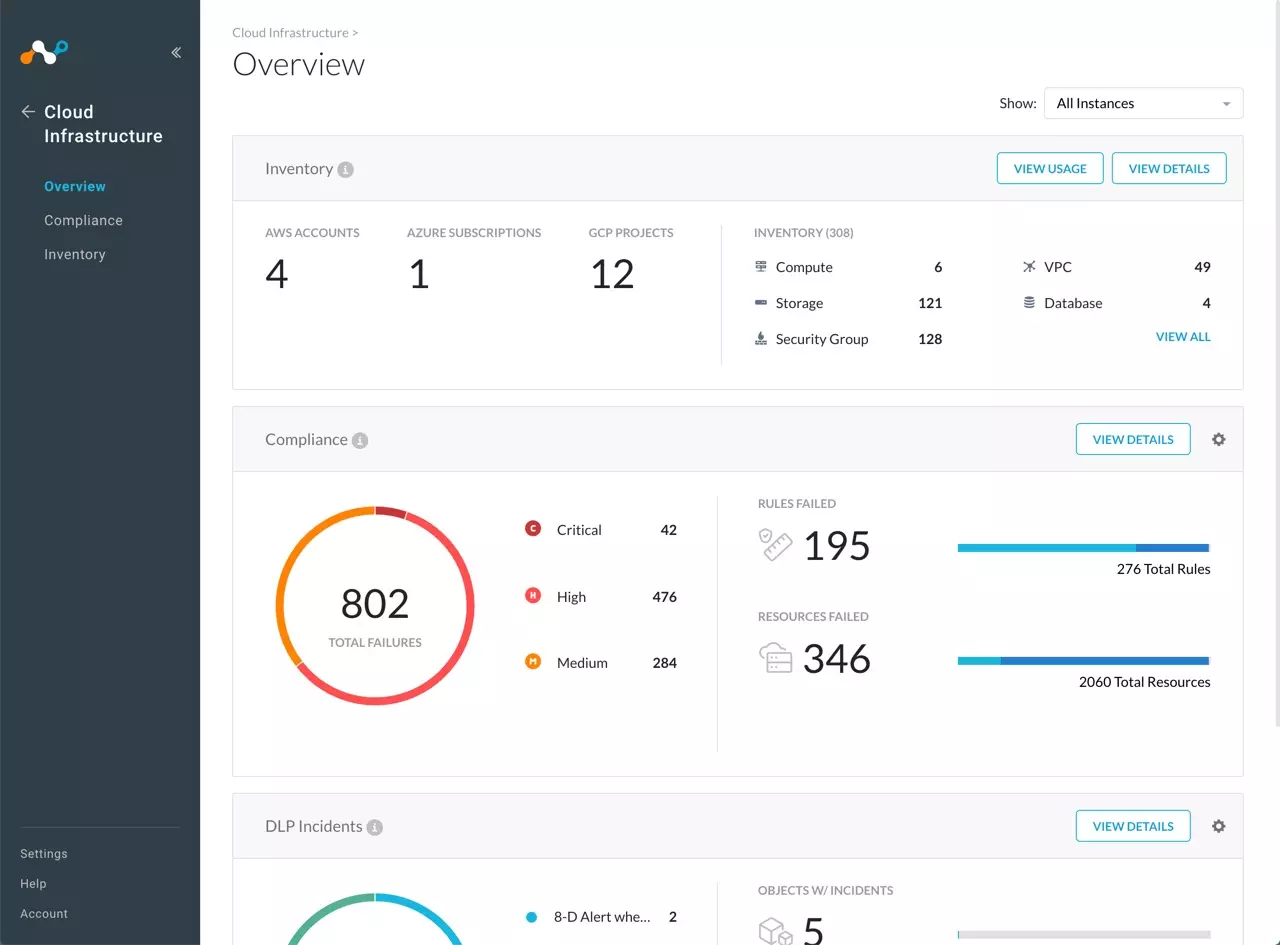
Cloud security standards and their support by prospective cloud service providers and within the enterprise is a critical area of focus for cloud service customers.
Cloud security guidelines and recommendations found in public private sources such as.
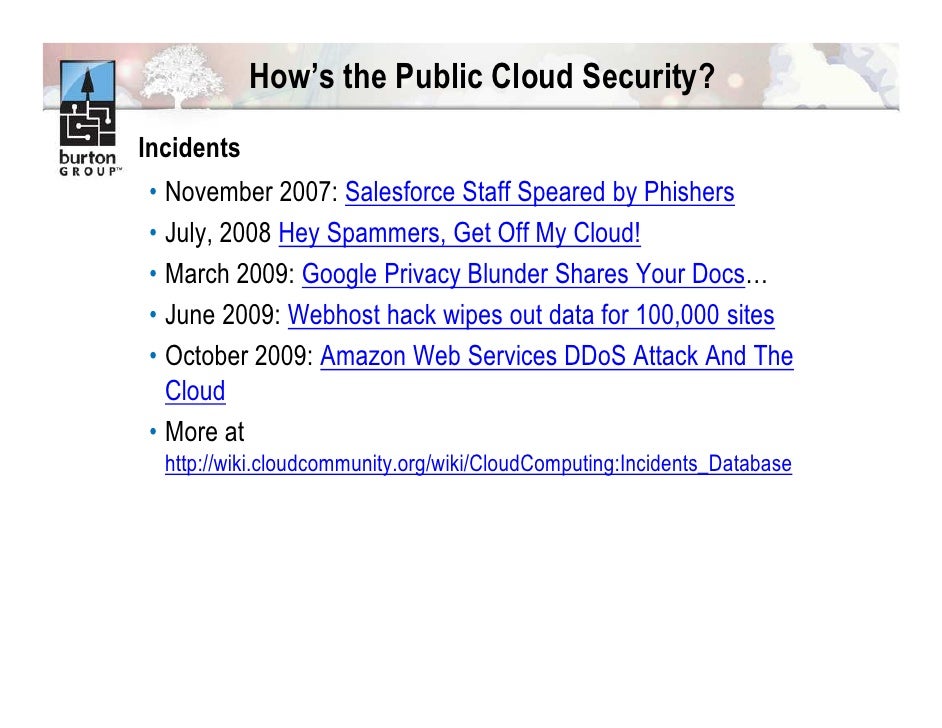
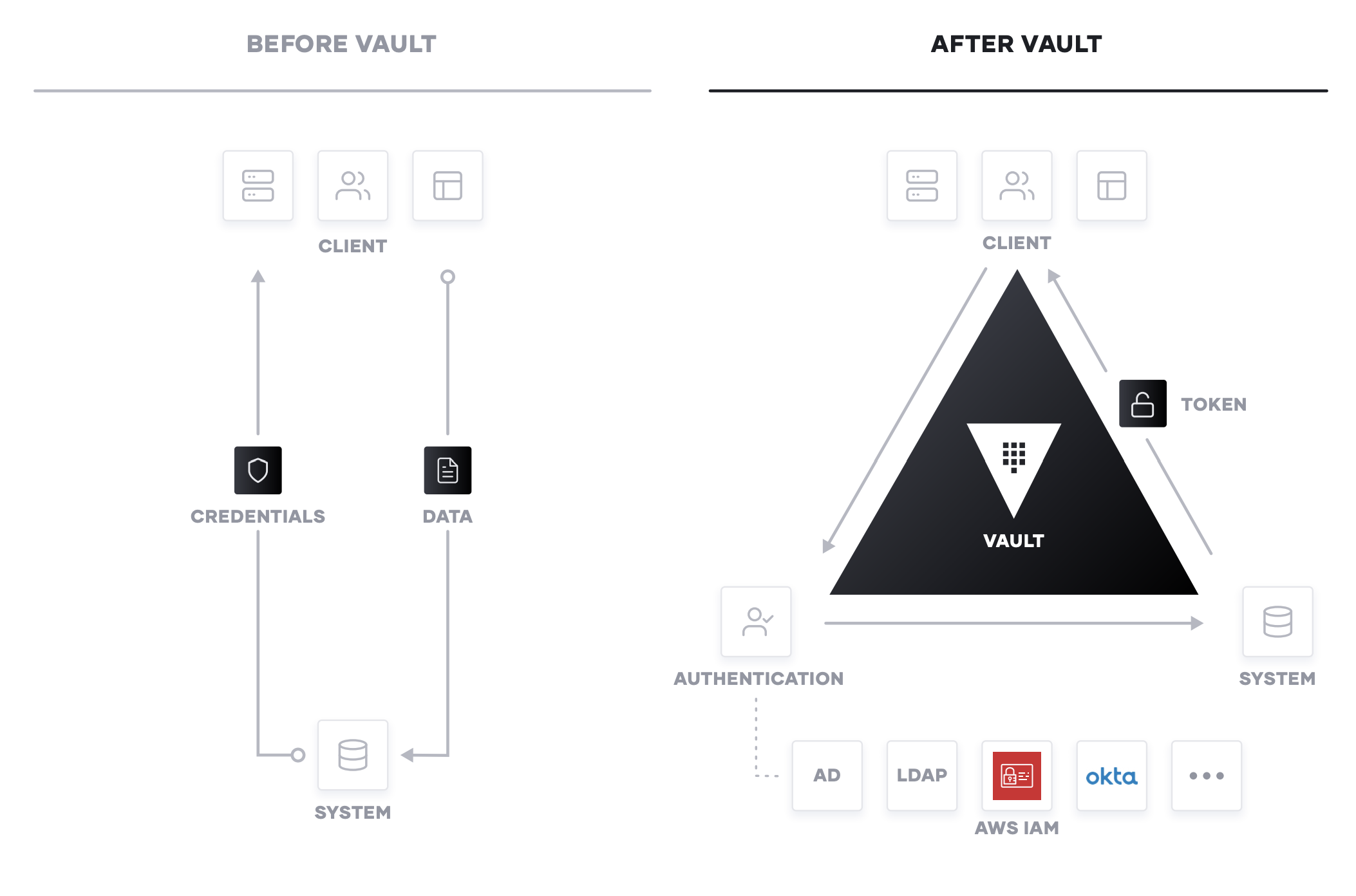
Recent cloud security incidents reported in the press such as unsecured aws storage services or the deloitte email compromise would most likely have been avoided if the cloud consumers had used security tools such as correctly configured access control encryption of data at rest and multi factor authentication offered by the csps.
It is intended to be used in conjunction with the information security objectives and controls found in iso iec 27002 2013 for creating a common set of security categories and controls for implementation by a public cloud computing service provider.
The landscape has matured with new cloud specific security standards like iso iec 27017 and iso iec 27018 for cloud computing security and privacy being adopted.
In this instance the public cloud service provider acts as the pii processor or the privacy.
The cloud security alliance csa is a leader in cloud security standard creation and implementation.
More specifically this document describes the threats technology risks and safeguards surrounding public cloud environments and their treatment.
While aspects of these characteristics have been.
The primary purpose of this report is to provide an overview of public cloud computing and the security and privacy considerations involved.