Since this technology is often used in an interactive setting efficiency and correctness are often the key user expectations from a system based on such technologies.
Program synthesis for interactive security systems.
We are tennessee s premier audio video installation and home security company serving franklin brentwood and the greater nashville and knoxville areas.
Program synthesis from incomplete specifications e g.
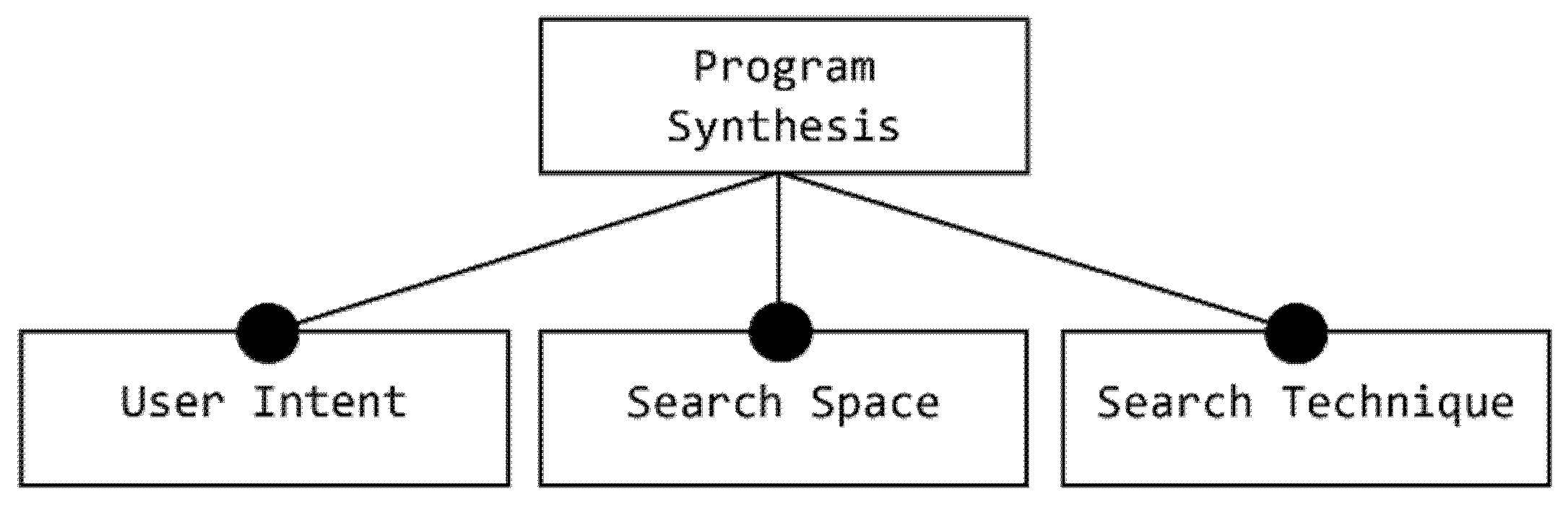
Introduction program synthesis is the task of generating a program in an underly ing domain specific language dsl from an intent specification pro vided by a user 3.
The basic control panel comes standard with all three plans and then you can customize your system by purchasing individual security products to connect.
Having installed over 300 intelligent ip security cameras locally within the past 12 months we have the necessary experience in engineering a system that will leverage the latest technology to create an interactive security system that delivers much more than just surveillance.
For two interactive security systems namely the capsicum capability system and the histar information flow system we developed languages of policies that a programmer can use to directly express security and functionality requirements along with synthesizers that take a program and policy in the language and generate a program that correctly.
Program synthesis is the task of automatically discovering an executable piece of code given user intent expressed using various forms of constraints such as input output examples demonstrations natural language etc.
Automatically learning the x86 64.
Google scholar digital library.
For two interactive security systems namely the capsicum capability system and the histar information flow system we developed languages of policies that a programmer can use to directly express security and functionality requirements along with synthesizers that take a program and policy in the language and generate a program that correctly uses system primitives to satisfy the policy.
Stefan heule eric schkufza rahul sharma and alex aiken.
Program synthesis for interactive security systems.
William r harris somesh jha thomas w reps and sanjit a seshia.
Link interactive offers some much needed flexibility because you can self monitor your security system or pay the monthly fee to have the professionals at link interactive monitor it for you.
Program synthesis for interactive security systems william harris somesh jha thomas reps sanjit seshia 11 30 12 00 a methodology to take credit for high level verification during rtl verification frederic doucet r.
51 2 2017 362 394.
Interactivity with respect to synthesis performance and correctness on a set of real world case studies.
Program synthesis has direct applications for various classes of users in the technology pyramid.